FAQ Overview
APP Customization
Index of Files need to be Customized
INSTALL
-
index.php
-
autoinstall.php
-
gotest.php
-
upgrade.php
-
logo.gif
LANGUAGES
-
language.inc.php
LANGUAGES > COUNTRIES
-
en.inc.php
-
es.inc.php
LANGUAGES > COMMON
-
en.inc.php (vonet + intemesh)
-
es.inc.php (vonet + intemesh)
-
en.js (line #53 - about)
-
es.js
ROOT
-
remider.php (groupoffice.ico to vonetoffice.ico)
-
group-office.php
-
dialog.php
-
default_scripts.inc.php
THEMES > SMARTY
-
footer.tpl (www)
THEMES > EXTJS
-
IMAGES / (groupoffice.ico to vonetoffice.ico)
-
default_head.inc.php
-
dialog.php
-
default_scripts.inc.php
THEMES > DEFAULT
-
IMAGES/(groupoffice.ico to vonetoffice.ico)
-
default_head.inc.php
-
layout.inc.php
-
default_scripts.inc.php (copyright / www)
JAVASCRIPT
-
MainLayout.js (HELP LINKS)
-
go-all-min (HELP LINKS)
CLASSES > MAIL
-
GoSwift.class.inc.php (From Line 185 - 189 / Group Office)
CLASSES > BASE
-
config.class.inc.php (Full File)
MODULES > EMAIL
-
register_email.php
MODULES > EMAIL > LANGUAGES
-
en.inc.php
-
es.inc.php
-
en.js (Settings / Links)
-
es.js en.js (Settings / Links)
MODULES > FILES
-
json.php (Lines 226 - 277 - Tree Structure MOD)
MODULES > FILES > LANGUAGES
-
en.inc.php
-
es.inc.php
MODULES > USERS > LANGUAGES
-
en.inc.php
-
es.inc.php
MODULES > SYSTEM USERS > LANGUAGES
-
en.inc.php
MODULES > SUMMARY > LANGUAGES
-
en.inc.php
-
es.inc.php
MODULES > SERVER CLIENT > LANGUAGES
-
en.inc.php
MODULES > POSTFIXADMIN > LANGUAGES
-
en.inc.php
MODULES > PHPBB3 > LANGUAGES
-
en.inc.php
MODULES > WORDPRESS > LANGUAGES
-
en.inc.php
MODULES > CMS > LANGUAGES
-
en.js
MODULES > BACKUPMANAGER > LANGUAGES
-
en.inc.php
-
en.js
MODULES > CUSTOMCSS > LANGUAGES
-
en.inc.php
MODULES > DOKUWIKI > LANGUAGES
-
en.inc.php
MODULES > MEDIAWIKI > LANGUAGES
-
en.inc.php
MODULES > IMAPAUTH > LANGUAGES
-
en.inc.php
MODULES > SETTINGS > LANGUAGES
-
en.inc.php
MODULES > SMIME > LANGUAGES
-
en.inc.php
Author: Luis Rosario
Last update: 04-05-2020 05:19
How to setup network after RHEL/CentOS 7 minimal
https://lintut.com/how-to-setup-network-after-rhelcentos-7-minimal-installation/
Comandos básico de network en CENTOS 7
nmcli d
nmtui
service network restart
Author: Luis Rosario
Last update: 08-05-2020 01:55
Magento Store Config File & Email Templates
Database Config
app/etc/local.xml
Email Templates
app/locale/en_US/template/email
Email Images
skin/frontend/default/default/images
Default Product Image
skin/frontend/default/theme/images/catalog/product/placeholder
Author: Luis Rosario
Last update: 04-05-2020 05:23
How to add a Contact Us form in Magento
Magento includes contact form functionality by default.
A link to a contact form can usually be found in the footer of your Magento installation.
Of course, you can add a contact form on any page. All you need to do is:
Paste the following code using the HTML option of the WYSIWYG editor:
<!– CONTACT FORM CODE BEGIN–>
{{block type='core/template' name='contactForm' template='contacts/form.phtml'}}
<!– CONTACT FORM CODE END–>
Save the changes and the contact form will appear on the desired page.
Author: Luis Rosario
Last update: 04-05-2020 05:26
How to disable the Compare products functionality
Edit app/code/core/Mage/Catalog/Helper/Product/Compare.php and change the following code:
public function getAddUrl($product)
{
return $this->_getUrl(’catalog/product_compare/add’, $this->_getUrlParams($product));
}
to
public function getAddUrl($product)
{
//return $this->_getUrl(’catalog/product_compare/add’, $this->_getUrlParams($product)); return false;
}
Edit ./app/design/frontend/base/default/layout/catalog.xml
(if you are using a different Magento theme, enter its name instead of default) and change the following code:
<block
name="catalog.compare.sidebar"
template="catalog/product/compare/sidebar.phtml"/>
to
<!-- <block
before="cart_sidebar" name="catalog.compare.sidebar"
template="catalog/product/compare/sidebar.phtml"/> -->
Flush the Magento cache from your Magento admin area > System > Cache Management.
Author: Luis Rosario
Last update: 04-05-2020 05:33
SPEEDTEST
http://binarynature.blogspot.com/2013/03/measure-internet-connection-speed-from-linux-command-line.html
Install Application
yum -y install git
Step #1
mkdir -p ~/repo/remote; cd $_
Step #2
git clone https://github.com/sivel/speedtest-cli.git
Step #3
mkdir ~/bin
Step #4
cp ~/repo/remote/speedtest-cli/speedtest_cli.py ~/bin/speedtest-cli
Step #5
cp ~/repo/remote/speedtest-cli/speedtest_cli.py /usr/local/bin/speedtest-cli
Search for a Server
speedtest-cli --list | grep -i guaynabo
2135) CLARO-PRT (Guaynabo, Puerto Rico) [14.68 km]
3657) Open Mobile (Guaynabo, Puerto Rico) [14.68 km]
SeedTest
speedtest-cli --server 3657 --share
Author: Luis Rosario
Last update: 04-05-2020 02:01
Unblock IP from Fail2Ban
SOURCE: http://help.webcontrolcenter.com/KB/a1023/unblock-ip-from-fail2ban.aspx
http://richardjh.org/blog/unblocking-fail2ban-hosts/
https://www.howtoforge.com/how-to-whitelist-an-ip-in-fail2ban-on-debian-wheezy
Login as root user and run command:
#iptables -L -n
Fail2Ban Blocked IP's Results:
Chain fail2ban-SSH (1 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0
To removed blocked IP Address - Substitute on the command: Service Name + IP Address :
# iptables -D fail2ban-SSH -s 72.50.53.40 -j DROP
Fail2Ban IP WHITELISTING:
# nano /etc/fail2ban/jail.conf
Then, check the line > Add IP + Save Changes:
# ignoreip = 127.0.0.1 207.204.159.100/28 67.206.208.221/28
Restart Fail2Ban:
# service fail2ban restart
Author: Luis Rosario
Last update: 04-05-2020 04:08
Fail2ban - Install Summary
SOURCE: Seguridad en Servidores 0-8-6.pdf
Login as root user and run command:
yum install fail2ban
CHECKLIST file to be Modify & Create:
etc/fail2ban/jail.conf
etc/fail2ban/filter.d/asterisk.conf
etc/asterisk/logger.conf
etc/rc.d/init.d/fail2ban
Start/Re-Start Fail2Ban Service:
service fail2ban restart
Verify Fail2ban is running:
ps ax | grep fail2ban
Start Fail2ban Everytime Server Power-Up/Re-Start:
chkconfig fail2ban on
Verify Fail2Ban Config for Errors:
fail2ban-regex /var/log/asterisk/full /etc/fail2ban/filter.d/asterisk.conf
Author: Luis Rosario
Last update: 04-05-2020 04:13
Firewall-Iptables
SOURCE: Seguridad en Servidores 0-8-6.pdf
Login as root user and run command:
iptables -A INPUT -s 192.168.0.0/24 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 5060 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 4569 -j ACCEPT
iptables -A INPUT -i eth0 -p udp -m udp --dport 10000:20000 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 80 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 443 -j ACCEPT
iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 22 -j ACCEPT
iptables -A INPUT -p all -i eth0 -j DROP
Verify Rules:
iptables -L
Reset/Erase Rules if something gets wrong: "FLUSH"
iptables -F
SAVE Rules:
/sbin/service iptables save
IPTABLES CONFIG FILE:
nano /etc/sysconfig/iptables
EXTRA RULES - OPENFIRE
iptables -A INPUT -p udp -m udp -i eth0 --dport 9090 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 7777 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 5222 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 9090 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 7777 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 5222 -j ACCEPT
Author: Luis Rosario
Last update: 04-05-2020 04:17
Change SSH port 22 to another one
SOURCE: http://www.liquidweb.com/kb/changing-the-ssh-port/
Backup Current Setup:
cp /etc/ssh/sshd_config /etc/ssh/sshd_config_backup
Edit and Change SSH Port from 22 to 20022:
nano /etc/ssh/sshd_config
Firewall - Open New Port and Close Old Port:
Edit Firewall Rules + Reboot Firewall
Reboot SSH Service:
/etc/init.d/sshd restart
Author: Luis Rosario
Last update: 04-05-2020 04:26
HD Get Full By Log Files
Access and Verify Log Folder
cd /var/log/asterisk/
ls -lah
Removed / Delete Log Files (As You want)
rm LOGFILE NAME
Author: Luis Rosario
Last update: 04-05-2020 04:31
Chan Spy
Source: http://www.freepbx.org/forum/chanspy-customization-in-freepbx
Edit File: extensions_override_freepbx.conf (For Permanent Effect)
extensions_additional.conf (For Tempotrary Effect)
Note: Authenticate(1234) - 1234 : is the password you want
[app-chanspy]
include => app-chanspy-custom
exten => 555,1,Authenticate(1234)
exten => 555,2,Read(SPYNUM,extension)
exten => 555,3,ChanSpy(SIP/${SPYNUM},q)
;old code
;exten => 555,1,Macro(user-callerid,)
;exten => 555,n,Answer
;exten => 555,n,Wait(1)
;exten => 555,n,ChanSpy()
;exten => 555,n,Hangup
; end of [app-chanspy]
Author: Luis Rosario
Last update: 04-05-2020 01:45
Monitoring Trunk Failures
SOURCE: http://zecic.com/monitoring-trunk-failures-in-freepbx/
Go into /var/lib/asterisk/agi-bin directory and create file alarm.agi and iax2alarm.agi.
Here is the content of the script:(NOTE: Modify SIP values for IAX values as required)
#!/bin/bash
EMAIL=luis@adnetgroup.com
DATE=date "+%d.%m.%Y. %H:%M"
HOST=hostname
# initializing agi variables
declare -a array
while read -e ARG && [ "$ARG" ] ; do
array=( echo $ARG | sed -e 's/://')
export ${array[0]}=${array[1]}
done
# SIP Trunk Status
SIPTRUNKS=/usr/sbin/asterisk -rx "sip show registry"
#Message
MESSAGE="Incident happend $DATE.\n$agi_calleridname [$agi_callerid]
tried to dial number $agi_dnid.\nCall could not be established on
channel $agi_channel."
MESSAGE="$MESSAGE\n\nCurrent SIP Trunk Status:\n$SIPTRUNKS"
# write log
echo "$DATE Call could not be established. $agi_calleridname
[$agi_callerid] --> $agi_dnid" >> /var/log/asterisk/trunk
# Reload trunk
/usr/sbin/asterisk -rx "sip reload"
# send email
echo -e "$MESSAGE" | mail -s "Incident at $HOST IP-PBX" "$EMAIL" -- -F "Asterisk"
Correct script ownership and permissions:
# chown asterisk:asterisk alarm.agi
# chown asterisk:asterisk iax2alarm.agi
# chmod +x alarm.agi
# chmod +x iax2alarm.agi
Check Permission:
ls -l
In /var/log/asterisk directory and create file trunk anc correct it’s ownership:
# > trunk
# chown asterisk:asterisk trunk
In FreePBX open trunks and select desired trunk.
Check Monitor Trunk Failures option and in the text box type alarm.agi:
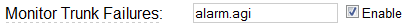
Apply changes in FreePBX and you are ready.
Keep in mind that trunk will also be log rotated like other logs in /var/log/asterisk.
Author: Luis Rosario
Last update: 04-05-2020 02:19
SPEEDTEST
http://binarynature.blogspot.com/2013/03/measure-internet-connection-speed-from-linux-command-line.html
Install Application
yum -y install git
Step #1
mkdir -p ~/repo/remote; cd $_
Step #2
git clone https://github.com/sivel/speedtest-cli.git
Step #3
mkdir ~/bin
Step #4
cp ~/repo/remote/speedtest-cli/speedtest_cli.py ~/bin/speedtest-cli
Step #5
cp ~/repo/remote/speedtest-cli/speedtest_cli.py /usr/local/bin/speedtest-cli
Search for a Server
speedtest-cli --list | grep -i guaynabo
2135) CLARO-PRT (Guaynabo, Puerto Rico) [14.68 km]
3657) Open Mobile (Guaynabo, Puerto Rico) [14.68 km]
SeedTest
speedtest-cli --server 3657 --share
Author: Luis Rosario
Last update: 04-05-2020 02:01
Asterisk CLI via SSH or Web
Inside SSH Terminal Type
asterisk -rvv
BASIC "CLI" COMMANDS
TRUNKS REGISTRY
sip show registry
iax2 show registry
RELOAD TRUNKS
sip reload
iax2 reload
TRUNK & EXTENSIONS STATUS
sip show peers
iax2 show peers
Author: Luis Rosario
Last update: 04-05-2020 02:17
Music On Hold - Custom
PART I - WEB BASED INTERFACE
1) Login to PBX Server: voip.vonetoffice.com (Example)
Username: admin
Password: xxxxxx
2) Access TAB MENU: PBX
> Look On PBX Vertical Menu For: Internal Options & Configuration
> Under Internal Options & Configuration Menu Options Access: Music On Hold
3) Music On Hold: Delete/Remove all Files
4) Music On Hold: Upload New (.Wav) Files
IMPORTANT> Wave File Specs: 8000HZ / 16bit / Mono
5) If You Many Audio Files: Enable Random Play
PART II - SSH TERMINAL
1) Audio Files Path:
/var/lib/asterisk/mohmp3/
2) Default Audio Files to be Removed: All (.gsm) and (.wav)
IMPORTANT> Be Careful: Don't Delete New UPLOADED (.Wav) Files
Author: Luis Rosario
Last update: 04-05-2020 02:24
TDM400P - FXO/FXS Hardware Card (Zaptel / Dahdi)
1) Login to PBX Server: voip.vonetoffice.com (example)
Username: admin
Password: xxxxxx
2) Access TAB MENU: PBX
> Access SUB-MENU: Tools
> Select Tool: File Editor or/ Asterisk File Editor
Look, Found and Access: chan_dahdi.conf and dahdi-channels.conf
3) Modify Files:
chan_dahdi.conf
x; Auto-generated by /usr/sbin/hardware_detector
[trunkgroups]
[channels]
;context=from-pstn
context=from-zaptel <<< ***ADD CODE***
signalling=fxs_ks
rxwink=300 ; Atlas seems to use long (250ms) winks
usecallerid=yes
hidecallerid=no
callwaiting=yes
usecallingpres=yes
callwaitingcallerid=yes
threewaycalling=yes
transfer=yes
canpark=yes
cancallforward=yes
callreturn=yes
echocancel=yes
echocancelwhenbridged=no
faxdetect=incoming
echotraining=800
rxgain=0.0
txgain=0.0
callgroup=1
pickupgroup=1
;Uncomment these lines if you have problems with the disconection of your analog lines
busydetect=yes
busycount=3
immediate=no
#include dahdi-channels.conf
#include chan_dahdi_additional.conf
dahdi-channels.conf
; Autogenerated by /usr/sbin/dahdi_genconf on Fri Feb 18 16:50:46 2011
; If you edit this file and execute /usr/sbin/dahdi_genconf again,
; your manual changes will be LOST.
; Dahdi Channels Configurations (chan_dahdi.conf)
;
; This is not intended to be a complete chan_dahdi.conf. Rather, it is intended
; to be #include-d by /etc/chan_dahdi.conf that will include the global settings
;
; Span 1: WCTDM/4 "Wildcard TDM400P REV E/F Board 5" (MASTER)
;;;
signalling=fxs_ks
callerid=asreceived
group=0
;context=from-pstn
context=from-zaptel <<< ***ADD CODE***
channel => 1
callerid=
group=
context=default
;;;
signalling=fxs_ks
callerid=asreceived
group=0
;context=from-pstn
context=from-zaptel <<< ***ADD CODE***
channel => 2
callerid=
group=
context=default
Author: Luis Rosario
Last update: 04-05-2020 02:28
Linksys - PAP2 - Factory Reset
PAP2 Factory Reset
WARNING! If you're using an unlocked PAP2 previously supplied by Vonage, your adapter will revert back to the settings from the factory after resetting and will immediately attempt to 'phone home', re-provisioning itself from Vonage! If you'd like to reset your PAP2 then re-unlock it, make sure that you disconnect it from the Internet prior to performing a factory reset!
Resetting your PAP2 to its factory default settings (often referred to as a 'hard reset') is done via the built-in IVR (Interactive Voice Response) menu. To access the IVR, simply pick up a telephone that is connected to the PAP2 and dial:
* * * *
(yep, 4 stars) This will activate the IVR 'Configuration Menu' (you'll hear a voice tell you this) after which point, simply press the following sequence of keys to 'factory reset' your PAP2:
7 3 7 3 8 #
Funnily enough, the above key sequence spells 'R E S E T', followed by a #. You'll be asked to confirm your selection - simply press 1 to continue. That's it.
Author: Luis Rosario
Last update: 04-05-2020 02:31
DNS Cache - Asterisk
SOURCE: http://www.c2s.co.nz/blog/sc-installing-pdns-recursor-in-elastix/
Install DNS Recursor:
yum -y install pdns-recursor
Edit Config File:
nano -w /etc/pdns-recursor/recursor.conf
#################################
# allow-from If set, only allow these comma separated netmasks to recurse
#
# allow-from=127.0.0.0/8, 10.0.0.0/8, 192.168.0.0/16, 172.16.0.0/12, ::1/128, f$
allow-from=127.0.0.0/8
#################################
Restart Service:
/etc/init.d/pdns-recursor restart
Access PBX Web Interface:
Change > Network Parameters
Primary DNS: 127.0.0.1
Verify Changes:
cat /etc/resolv.conf
Author: Luis Rosario
Last update: 04-05-2020 02:46
Monitoring - Recording Files Access
How to create direct access to MONITORING folder to backup recorded files from PBX Server.
STEP #1 : ADD USER & PASSWORD
# adduser ******VONETPBX*****
# passwd *****PASSWORD*****
STEP #2 CREATE A SYMBOLIC FOLDER - MONITORING
# cd /home/vonetpbx
# ln -s /var/spool/asterisk/monitor monitor
# chown -h vonetpbx:vonetpbx monitor
STEP #3 TEST ACCOUNT - SFTP CONNECTION
You can use filezilla.org application client.
Author: Luis Rosario
Last update: 04-05-2020 02:51
STOP Recordings (Always Rec)
features_applicationmap_custom.conf
pauseMonitor => *881,peer/callee,StopMixMonitor()
globals_custom.conf
DYNAMIC_FEATURES=>pauseMonitor
SSH
asterisk -rx "dialplan reload"
asterisk -rx "features reload"
asterisk -rx "features show"
You must find the feature added in Dynamoc Feature list
Dynamic Feature Default Current
--------------- ------- -------
pauseMonitor no def *881
General Settings:
Asterisk Dial command options: trWW
Asterisk Outbound Dial command options: wW
Now on incoming call, press *8811 to stop the recording.
Author: Luis Rosario
Last update: 04-05-2020 02:57
Change default CentOS text editor from VI to Nano
SOURCE: http://www.khmer365.com/index.php?topic=3791.0
To change default VI Editor to Nano (Temporary)> Type the command as follows:
-
which nano
-
export EDITOR=/usr/bin/nano
-
crontab -e
To change default VI Editor to Nano (Permanent) > Type the command as follows:
nano /etc/profile
To change default VI Editor to Nano (Permanent) > ADD This Code to Profile:
export EDITOR=/usr/bin/nano
Author: Luis Rosario
Last update: 04-05-2020 03:19
Hotel - Management System
http://blogs.elastix.org/en/2010/03/how-to-hotel-management-system/
1) Installing the base system
First you’re going to need to ssh in to your Elastix PBX System.
Then, run the following:
cd /var/www/html
wget http://www.kefa.it/hotel.tar.gz
tar zxvf hotel.tar.gz
rm hotel.tar.gz
cd hotel
mysql -uroot -pPASSWORD < Hotel.sql
2) Updating the config
nano -w config.inc.php
Now you’re going to modify the following three paragraphs so that they match below:
//Hotel database
$dbhost = "localhost";
$dbpass = "PASSWORD";
$dbuser = "root";
$dbname = "Hotel";
//Asterisk database
$dbhost2 = "localhost";
$dbpass2 = "PASSWORD";
$dbuser2 = "root";
$dbname2 = "asterisk";
//Asteriskcdrdb database
$dbhost3 = "localhost";
$dbpass3 = "PASSWORD";
$dbuser3 = "root";
$dbname3 = "asteriskcdrdb"
Save and exit and you’re done with the config.
3) Fixing up HTTPS
nano /etc/httpd/conf.d/elastix.conf
MODIFY these line on elastix.conf file:
RewriteEngine Off
//////////// Second Option ///////////////////
# Redirect administration interface to https
RewriteEngine on
RewriteCond %{HTTPS} off
RewriteCond %{REQUEST_URI} !(/hotel/*) RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
Now, restart apache with:
/etc/init.d/httpd restart
You should now be able to access your WebGUI without HTTPS at:
http://pbxip/hotel/
If not, then go back and try again, as this part is crucial to the redirection to Reception when a phone is not Checked In
4) Updating dial-plan
Now we’re going to add in to the Dial-Plan and tell the PBX what calls can and cannot be made when the phone is not Checked-In.
nano /etc/asterisk/extensions_custom.conf
ADD the following underneath the [from-internal-custom] header:
;lets guests call other rooms without being checked in
;exten => _XXX,1,Dial(SIP/${EXTEN})
;exten => _XXX,n,Hangup()
;provide access to specific extensions without being checked in
exten => _128,1,Dial(SIP/${EXTEN})
exten => _128,n,Hangup()
exten => _13X,1,Dial(SIP/${EXTEN})
exten => _13X,n,Hangup()
exten => _14X,1,Dial(SIP/${EXTEN})
exten => _14X,n,Hangup()
exten => _15X,1,Dial(SIP/${EXTEN})
exten => _15X,n,Hangup()
exten => _5X,1,Dial(SIP/${EXTEN})
exten => _5X,n,Hangup()
;lets guests call freephonenumbers without being checked in
;exten => _1800NXXXXXX,1,Goto(outbound-allroutes,${EXTEN},1)
;exten => _1800NXXXXXX,n,Hangup()
exten => _X.,1,Set(result=${CURL(http://127.0.0.1/hotel/checkuser.php?Ext=${CALLERID(num)})})
exten => _X.,n,NoOp(Results: ${result})
exten => _X.,n,GotoIf($["${result}" = "OK"]?OK)
exten => _X.,n,GotoIf($["${result}" = "KO"]?KO)
exten => _X.,n(OK),Goto(outbound-allroutes,${EXTEN},1)
exten => _X.,n,Hangup()
;call front desk if not checked in
exten => _X.,n(KO),Dial(SIP/130) ; used for just one extension
;exten => _X.,n(KO),Goto(ext-group,2,1) ; used for ring groups
exten => _X.,n,Hangup()
;Hotel Management Configuration
exten => XXX,1,Dial(SIP/${DIAL})
exten => _X.,2,Macro(user-callerid,)
exten => _X.,3,Set(result=${CURL(http://127.0.0.1/hotel/checkuser.php?Ext=${CALLERID(num)})})
exten => _X.,4,NoOp(Results: ${result})
exten => _X.,5,GotoIf($["${result}" = "OK"]?OK)
exten => _X.,6,GotoIf($["${result}" = "KO"]?KO)
exten => _X.,7(OK),Goto(outbound-allroutes,${EXTEN},1)
exten => _X.,8,Hangup()
exten => _X.,9(KO),Dial(SIP/150) ; used for just one extension
;exten => _X.,n(KO),Goto(ext-group,2,1) ; used for ring groups
exten => _X.,10,Hangup()
Save the file and run:
asterisk -rx "dialplan reload"
Author: Luis Rosario
Last update: 04-05-2020 03:44
Call Recordings - Server Maintenance
1) Create Folder: mkdir /etc/recordingdeletion/
2) Create File Inside Folder: nano OldRecordingDeletion.sh
#!/bin/bash
# Change this path to reflect your recording storage
# location
RECORDINGS=/var/spool/asterisk/monitor
# Change this number to reflect the maximum age of call
# recordings
RECORDINGEXPIRY=14
# Change this number to reflect the maximum age of the
# deletion logs
LOGEXPIRY=25
# Current date
DATE=´date´
# Delete recordings older than $EXPIRY days
find $RECORDINGS -mtime +$RECORDINGEXPIRY > "removal-$DATE.log"
find $RECORDINGS -mtime +$RECORDINGEXPIRY -exec rm -f {} \;
# Delete log files older than $LOGEXPRY
find . -mtime +$LOGEXPIRY -name "*.log" -exec rm -f {} \;
3) Apply Permission: chmod +x OldRecordingDeletion.sh
4) Check Permission: ls -l
5) Create CRON JOB on Server: crontab -e
0 4 * * * /etc/recordingdeletion/OldRecordingDeletion.sh
6) Check CRON JOB Creation: nano /var/spool/cron/root
7) CRON JOB Log Files: tail -f /var/log/cron
Author: Luis Rosario
Last update: 04-05-2020 03:50
G729 / G723 Codecs - Installation (Open Source Version)
Source: http://www.blog.manhag.org/2010/05/installing-the-free-g729-codec-for-asterisk
Check Asterisk Version
Login to PBX Server: voip.vonetoffice.com (Example)
Username: admin
Password: xxxxxx
Access TAB MENU: PBX
> Access SUB-MENU: Tools
> Select Tool: Asterisk-Cli
Command: CORE SHOW VERSION
[Execute]
Common Used Codecs
Asterisk 1.4
codec_g723-ast14-gcc4-glibc-pentium4.so
codec_g729-ast14-gcc4-glibc-pentium4.so
codec_g723-ast14-gcc4-glibc-atom.so
codec_g729-ast14-gcc4-glibc-atom.so
Asterisk 1.6
codec_g723-ast16-gcc4-glibc-pentium4.so
codec_g729-ast16-gcc4-glibc-pentium4.so
codec_g723-ast16-gcc4-glibc-atom.so
codec_g729-ast16-gcc4-glibc-atom.so
1) Download Codec and Rename
Download: http://asterisk.hosting.lv
Rename:
codec_g723.so
codec_g729.so
2) Asterisk Server - Codec Upload Path:
/usr/lib/asterisk/module/
3) Restart Asterisk
/etc/init.d/asterisk restart
4) Login to PBX Server: voip.vonetoffice.com (Example)
Username: admin
Password: xxxxxx
5) Access TAB MENU: PBX
> Access SUB-MENU: Tools
> Select Tool: Asterisk-Cli
Command: core show translation
[Execute]
6) Asterisk Results
Translation times between formats (in microseconds) for one second of data
Source Format (Rows) Destination Format (Columns)
g723 gsm ulaw alaw g726aal2 adpcm slin lpc10 g729 speex ilbc g726 g722 siren7 siren14 slin16
g723 - 4999 1001 1001 3999 1001 1000 3999 11998 18998 - 4999 3000 - - 4999
gsm 13998 - 2001 2001 4999 2001 2000 4999 12998 19998 - 5999 4000 - - 5999
ulaw 11999 4000 - 1 3000 2 1 3000 10999 17999 - 4000 2001 - - 4000
alaw 11999 4000 1 - 3000 2 1 3000 10999 17999 - 4000 2001 - - 4000
g726aal2 12998 4999 1001 1001 - 1001 1000 3999 11998 18998 - 4999 3000 - - 4999
adpcm 11999 4000 2 2 3000 - 1 3000 10999 17999 - 4000 2001 - - 4000
slin 11998 3999 1 1 2999 1 - 2999 10998 17998 - 3999 2000 - - 3999
lpc10 13998 5999 2001 2001 4999 2001 2000 - 12998 19998 - 5999 4000 - - 5999
g729 14998 6999 3001 3001 5999 3001 3000 5999 - 20998 - 6999 5000 - - 6999
speex 14997 6998 3000 3000 5998 3000 2999 5998 13997 - - 6998 4999 - - 6998
ilbc - - - - - - - - - - - - - - - -
g726 13998 5999 2001 2001 4999 2001 2000 4999 12998 19998 - - 4000 - - 5999
g722 13998 5999 2001 2001 4999 2001 2000 4999 12998 19998 - 5999 - - - 1999
siren7 - - - - - - - - - - - - - - - -
siren14 - - - - - - - - - - - - - - - -
slin16 16998 8999 5001 5001 7999 5001 5000 7999 15998 22998 - 8999 3000 - - -
Author: Luis Rosario
Last update: 04-05-2020 03:56
Conference Calls - Recorded Files Storage
Recorded Conference Calls are SAVED on Server's Path:
/var/spool/asterisk/monitor
Author: Luis Rosario
Last update: 04-05-2020 03:58
Unblock IP from Fail2Ban
SOURCE: http://help.webcontrolcenter.com/KB/a1023/unblock-ip-from-fail2ban.aspx
http://richardjh.org/blog/unblocking-fail2ban-hosts/
https://www.howtoforge.com/how-to-whitelist-an-ip-in-fail2ban-on-debian-wheezy
Login as root user and run command:
#iptables -L -n
Fail2Ban Blocked IP's Results:
Chain fail2ban-SSH (1 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0
To removed blocked IP Address - Substitute on the command: Service Name + IP Address :
# iptables -D fail2ban-SSH -s 72.50.53.40 -j DROP
Fail2Ban IP WHITELISTING:
# nano /etc/fail2ban/jail.conf
Then, check the line > Add IP + Save Changes:
# ignoreip = 127.0.0.1 207.204.159.100/28 67.206.208.221/28
Restart Fail2Ban:
# service fail2ban restart
Author: Luis Rosario
Last update: 04-05-2020 04:08
Fail2ban - Install Summary
SOURCE: Seguridad en Servidores 0-8-6.pdf
Login as root user and run command:
yum install fail2ban
CHECKLIST file to be Modify & Create:
etc/fail2ban/jail.conf
etc/fail2ban/filter.d/asterisk.conf
etc/asterisk/logger.conf
etc/rc.d/init.d/fail2ban
Start/Re-Start Fail2Ban Service:
service fail2ban restart
Verify Fail2ban is running:
ps ax | grep fail2ban
Start Fail2ban Everytime Server Power-Up/Re-Start:
chkconfig fail2ban on
Verify Fail2Ban Config for Errors:
fail2ban-regex /var/log/asterisk/full /etc/fail2ban/filter.d/asterisk.conf
Author: Luis Rosario
Last update: 04-05-2020 04:13
Firewall-Iptables
SOURCE: Seguridad en Servidores 0-8-6.pdf
Login as root user and run command:
iptables -A INPUT -s 192.168.0.0/24 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 5060 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 4569 -j ACCEPT
iptables -A INPUT -i eth0 -p udp -m udp --dport 10000:20000 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 80 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 443 -j ACCEPT
iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 22 -j ACCEPT
iptables -A INPUT -p all -i eth0 -j DROP
Verify Rules:
iptables -L
Reset/Erase Rules if something gets wrong: "FLUSH"
iptables -F
SAVE Rules:
/sbin/service iptables save
IPTABLES CONFIG FILE:
nano /etc/sysconfig/iptables
EXTRA RULES - OPENFIRE
iptables -A INPUT -p udp -m udp -i eth0 --dport 9090 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 7777 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 5222 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 9090 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 7777 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 5222 -j ACCEPT
Author: Luis Rosario
Last update: 04-05-2020 04:17
Password Protect
nano /etc/httpd/conf.d/elastix.conf
<Directory "/var/www/html">
# Redirect administration interface to https
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
AuthType Basic
AuthName "PRIVATE ACCESS"
AuthUserFile /usr/local/apache/wwwpasswd
Require user elastix admin ciqala
</Directory>
mkdir /usr/local/apache
htpasswd –c /usr/local/apache/wwwpasswd admin
service httpd restart
EXTRA USERS
htpasswd /usr/local/apache/wwwpasswd ciqala
service httpd restart
Author: Luis Rosario
Last update: 04-05-2020 04:21
Removed VTiger CRM
Removed vtiger from the server
rpm -e elastix-vtigercrm
Author: Luis Rosario
Last update: 04-05-2020 04:23
Change SSH port 22 to another one
SOURCE: http://www.liquidweb.com/kb/changing-the-ssh-port/
Backup Current Setup:
cp /etc/ssh/sshd_config /etc/ssh/sshd_config_backup
Edit and Change SSH Port from 22 to 20022:
nano /etc/ssh/sshd_config
Firewall - Open New Port and Close Old Port:
Edit Firewall Rules + Reboot Firewall
Reboot SSH Service:
/etc/init.d/sshd restart
Author: Luis Rosario
Last update: 04-05-2020 04:26
LVM Partitions
SOURCE: http://www.how2centos.com/centos-lvm-resizing-guide/
STEP #1
lvresize -L +4GB /dev/VolGroup00/LogVol00
STEP #2
resize2fs -p /dev/VolGroup00/LogVol00
Author: Luis Rosario
Last update: 04-05-2020 04:29
HD Get Full By Log Files
Access and Verify Log Folder
cd /var/log/asterisk/
ls -lah
Removed / Delete Log Files (As You want)
rm LOGFILE NAME
Author: Luis Rosario
Last update: 04-05-2020 04:31
FOP2 - Different LAN CARD (eth0 is Default)
STEP #1 - Remover licencia / registro
If you plan to change network hardware or configuration, or reinstall your server, you *must* revoke the FOP2 license prior to that, with the command:
/usr/local/fop2/fop2_server --revoke
That action will free up your activation code to be used again after your changes/reinstallation.
STEP #2 - Registrar licencia via SSH
/usr/local/fop2/fop2_server --register -i eth1
STEP #3 - Configurar la tarjeta que utilizara FOP2
nano /etc/sysconfig/fop2
OPTIONS="-d -c /etc/asterisk/fop2 -i eth1"
service fop2 restart
Author: Luis Rosario
Last update: 04-05-2020 04:34
Adding Second HD (Hard Drive)
STEP #1 - Verify if Server detect HD
cat /proc/partitions
STEP #2 - Verify if HD is Mount
df -h
STEP #3 - Create HD Mount Point
mkdir /monitor
STEP #4 - Change Folder Permissions
chgrp asterisk /monitor
chown asterisk /monitor
ls -al
STEP #5 - Edit Server's Boot File
nano /etc/rc.local
ADD THIS CODE:
/bin/mount /dev/sdb1 /monitor
STEP #6 - Execute Server's Boot Script
cd /etc
./rc.local
STEP #7 - Verify HD Mounting Point
df -h
STEP #8- Verify Recording Location (To Backup Old Recordings)
cd /var/spool/asterisk/monitor/
ls
mv ./* /monitor
cd
STEP #9 - Removed Recording Folder + Create a Symbolic Link to New Folder
rm -rf /var/spool/asterisk/monitor
/bin/ln -s /monitor /var/spool/asterisk
STEP #10 - Verify Symbolic Link to New Folder
cd /var/spool/asterisk
ls -l
STEP #11 - Change Folder Permissions to Prevent Writing Errors
chown -h asterisk:asterisk monitor
ls -l
Author: Luis Rosario
Last update: 04-05-2020 04:47
How to list all DND-enable extensions
Source: http://www.mehrdust.com/archives/how-to-list-all-dnd-enable-extensions
in linux prompt run:
# asterisk -rx “database show DND”
# asterisk -rx “database show” | grep “/DND/”
# asterisk -rx "database show DND"
/DND/1002 : YES
/DND/1004 : YES
/DND/1006 : YES
/DND/1007 : YES
To remove DND from an extension run:
# asterisk -rx “database del DND ext.”
To enable DND manully for an extension run:
# asterisk -rx “database put DND ext. YES”
# asterisk -rx "database put DND 1002 YES"
Updated database successfully
# asterisk -rx "database show DND" /DND/1002 : YES
Author: Luis Rosario
Last update: 04-05-2020 04:56
LAN Card - Name Change
1) Removed & Rename the network interface configuration file :
cd etc/sysconfig/network-scripts/
rm ifcfg-eth0
mv ifcfg-eth1 ifcfg-eth0
2) Edit the network interface configuration file and replace all occurrences of the old name eth1 with the new one eth0 :
nano /etc/sysconfig/network-scripts/ifcfg-eth0
3) Removed & Rename the network interface configuration file :
cd etc/sysconfig/networking/devices
rm ifcfg-eth0
mv ifcfg-eth1 ifcfg-eth0
cd etc/sysconfig/networking/profiles/default
rm ifcfg-eth0
mv ifcfg-eth1 ifcfg-eth0
Author: Luis Rosario
Last update: 04-05-2020 05:12
Voicemail Recordings
Files Path
var/spool/asterisk/voicemail/default/100/
Author: Luis Rosario
Last update: 04-05-2020 05:15
How to setup network after RHEL/CentOS 7 minimal
https://lintut.com/how-to-setup-network-after-rhelcentos-7-minimal-installation/
Comandos básico de network en CENTOS 7
nmcli d
nmtui
service network restart
Author: Luis Rosario
Last update: 08-05-2020 01:55
Issabel CDR - Don't Show Source Caller ID
SOURCE: https://forum.issabel.org/d/3462-no-source-in-cdr-records/5
the query should be fixed in /var/www/html/libs/paloSantoCDR.class.php
Line 238 : replace "IF(cnum<>src,cnum,src)" with "IF(cnum<>src,IF(cnum<>0,cnum,src),src)"
Author: Luis Rosario
Last update: 25-03-2021 02:10
GXW410X - Grandstream Gateway
STEP #1 - CONFIGURATION

STEP #2 - CONFIGURATION

STEP #3 - CONFIGURATION

STEP #4 - CONFIGURATION

STEP #5 - CONFIGURATION

STEP #6 - CONFIGURATION

STEP #7 - SIP TRUNK
Trunk Name: Username #
PEER Details:
type=peer
secret=PASSWORD
insecure=very
host=dynamic
qualify=yes
Author: Luis Rosario
Last update: 04-05-2020 01:31
Grandstream HT503 (FXO)
STEP #1 - SIP TRUNK
Trunk Name: Username #
PEER Details:
secret=PASSWORD
dtmfmode=rfc2833
canreinvite=no
context=from-trunk
host=dynamic
type=friend
port=5062
qualify=yes
disallow=all
allallow=ulaw,g729
STEP #2 - Grandstream HT503 SETUP
Ver PDF para detalles
Author: Luis Rosario
Last update: 04-05-2020 01:39
TDM400P - FXO/FXS Hardware Card (Zaptel / Dahdi)
1) Login to PBX Server: voip.vonetoffice.com (example)
Username: admin
Password: xxxxxx
2) Access TAB MENU: PBX
> Access SUB-MENU: Tools
> Select Tool: File Editor or/ Asterisk File Editor
Look, Found and Access: chan_dahdi.conf and dahdi-channels.conf
3) Modify Files:
chan_dahdi.conf
x; Auto-generated by /usr/sbin/hardware_detector
[trunkgroups]
[channels]
;context=from-pstn
context=from-zaptel <<< ***ADD CODE***
signalling=fxs_ks
rxwink=300 ; Atlas seems to use long (250ms) winks
usecallerid=yes
hidecallerid=no
callwaiting=yes
usecallingpres=yes
callwaitingcallerid=yes
threewaycalling=yes
transfer=yes
canpark=yes
cancallforward=yes
callreturn=yes
echocancel=yes
echocancelwhenbridged=no
faxdetect=incoming
echotraining=800
rxgain=0.0
txgain=0.0
callgroup=1
pickupgroup=1
;Uncomment these lines if you have problems with the disconection of your analog lines
busydetect=yes
busycount=3
immediate=no
#include dahdi-channels.conf
#include chan_dahdi_additional.conf
dahdi-channels.conf
; Autogenerated by /usr/sbin/dahdi_genconf on Fri Feb 18 16:50:46 2011
; If you edit this file and execute /usr/sbin/dahdi_genconf again,
; your manual changes will be LOST.
; Dahdi Channels Configurations (chan_dahdi.conf)
;
; This is not intended to be a complete chan_dahdi.conf. Rather, it is intended
; to be #include-d by /etc/chan_dahdi.conf that will include the global settings
;
; Span 1: WCTDM/4 "Wildcard TDM400P REV E/F Board 5" (MASTER)
;;;
signalling=fxs_ks
callerid=asreceived
group=0
;context=from-pstn
context=from-zaptel <<< ***ADD CODE***
channel => 1
callerid=
group=
context=default
;;;
signalling=fxs_ks
callerid=asreceived
group=0
;context=from-pstn
context=from-zaptel <<< ***ADD CODE***
channel => 2
callerid=
group=
context=default
Author: Luis Rosario
Last update: 04-05-2020 02:28
Linksys - PAP2 - Factory Reset
PAP2 Factory Reset
WARNING! If you're using an unlocked PAP2 previously supplied by Vonage, your adapter will revert back to the settings from the factory after resetting and will immediately attempt to 'phone home', re-provisioning itself from Vonage! If you'd like to reset your PAP2 then re-unlock it, make sure that you disconnect it from the Internet prior to performing a factory reset!
Resetting your PAP2 to its factory default settings (often referred to as a 'hard reset') is done via the built-in IVR (Interactive Voice Response) menu. To access the IVR, simply pick up a telephone that is connected to the PAP2 and dial:
* * * *
(yep, 4 stars) This will activate the IVR 'Configuration Menu' (you'll hear a voice tell you this) after which point, simply press the following sequence of keys to 'factory reset' your PAP2:
7 3 7 3 8 #
Funnily enough, the above key sequence spells 'R E S E T', followed by a #. You'll be asked to confirm your selection - simply press 1 to continue. That's it.
Author: Luis Rosario
Last update: 04-05-2020 02:31
Linksys/Cisco SPA3102
http://www.stephenwagner.com/?p=362
Author: Luis Rosario
Last update: 04-05-2020 05:17
VOZPR - Sip Trunk
Outbound Caller ID: "Company Name" <17878900017>
Trunk Name: Client or Phone Number
PEER Details:
username=xxxxx
type=peer
secret=xxxxxx
nat=yes
insecure=very
host=209.91.245.5
fromdomain=sip-proxy.vozpr.com
disallow=all
context=from-pstn
allow=g723.1&g729&ulaw&alaw
USER Context: username xxxxxxxx
USER Details:
useragent=ast_pbx
qualify=yes
port=5060
nat=yes
insecure=very
host=209.91.245.5
disallow=all
context=from-pstn
canreinvite=no
allow=g723.1&g729&ulaw&alaw
Register String:
username:password@sip-proxy.vozpr.com
Author: Luis Rosario
Last update: 04-05-2020 01:16
Liberty - IP TRUNK
PASO #1 : Via SSH crear ruta para Tarjeta de LAN
(Importante: remplazar eth# con el numero de la tarjeta que se utilizara)
nano /etc/sysconfig/network-scripts/route-eth2
24.50.198.0/29 via 10.250.17.1 dev eth2
Guardar "Save"
"Reboot" al Server
PASO #2 : Crear SIP TRUNK
Outbound Caller ID: # Numero Piloto
Trunk Name: liberty-out
PEER Details:
host=24.50.198.7
type=peer
disallow=all
allow=ulaw
nat=no
insecure=port,invite
USER Context: liberty-in
USER Details:
type=user
context=from-trunk
Author: Luis Rosario
Last update: 04-05-2020 01:03
AT&T - IP TRUNK
PASO #1 : Via SSH crear ruta para Tarjeta de LAN
(Importante: remplazar eth# con el numero de la tarjeta que se utilizara)
nano /etc/sysconfig/network-scripts/route-eth2
24.50.198.0/29 via 10.250.17.1 dev eth2
Guardar "Save"
"Reboot" al Server
PASO #2 : Crear SIP TRUNK
Outbound Caller ID: # Numero Piloto
Trunk Name: AT&T
PEER Details:
username=787XXXXXXX
type=friend
secret=PASSWORD
nat=no
insecure=invite
host=172.31.255.254
fromdomain=172.31.255.250
dtmfmode=rfc2833
disallow=all
canreinvite=no
allow=ulaw
Register String:
787XXXXXXX:PASSWORD@172.31.255.254/787XXXXXXX
Author: Luis Rosario
Last update: 04-05-2020 01:09
WORLDNET - Sip Trunk
Outbound Caller ID: # Numero Telefono
Trunk Name: worldnet
PEER Details:
username=xxxxxx
type=friend
trustrpid=yes
sendrpid=yes
secret=xxxxxx
nat=yes
insecure=port,invite
host=sipa.wntpr.net
fromuser=xxxxxx
dtmfmode=rfc2833
USER Context: username xxxxxxxxxx
USER Details:
type=user
secret=xxxxxxxxx
context=from-trunk
Register String:
username:password@sipa.wntpr.net:5060/username
Author: Luis Rosario
Last update: 04-05-2020 01:18
GXW410X - Grandstream Gateway
STEP #1 - CONFIGURATION

STEP #2 - CONFIGURATION

STEP #3 - CONFIGURATION

STEP #4 - CONFIGURATION

STEP #5 - CONFIGURATION

STEP #6 - CONFIGURATION

STEP #7 - SIP TRUNK
Trunk Name: Username #
PEER Details:
type=peer
secret=PASSWORD
insecure=very
host=dynamic
qualify=yes
Author: Luis Rosario
Last update: 04-05-2020 01:31
Grandstream HT503 (FXO)
STEP #1 - SIP TRUNK
Trunk Name: Username #
PEER Details:
secret=PASSWORD
dtmfmode=rfc2833
canreinvite=no
context=from-trunk
host=dynamic
type=friend
port=5062
qualify=yes
disallow=all
allallow=ulaw,g729
STEP #2 - Grandstream HT503 SETUP
Ver PDF para detalles
Author: Luis Rosario
Last update: 04-05-2020 01:39
Monitoring Trunk Failures
SOURCE: http://zecic.com/monitoring-trunk-failures-in-freepbx/
Go into /var/lib/asterisk/agi-bin directory and create file alarm.agi and iax2alarm.agi.
Here is the content of the script:(NOTE: Modify SIP values for IAX values as required)
#!/bin/bash
EMAIL=luis@adnetgroup.com
DATE=date "+%d.%m.%Y. %H:%M"
HOST=hostname
# initializing agi variables
declare -a array
while read -e ARG && [ "$ARG" ] ; do
array=( echo $ARG | sed -e 's/://')
export ${array[0]}=${array[1]}
done
# SIP Trunk Status
SIPTRUNKS=/usr/sbin/asterisk -rx "sip show registry"
#Message
MESSAGE="Incident happend $DATE.\n$agi_calleridname [$agi_callerid]
tried to dial number $agi_dnid.\nCall could not be established on
channel $agi_channel."
MESSAGE="$MESSAGE\n\nCurrent SIP Trunk Status:\n$SIPTRUNKS"
# write log
echo "$DATE Call could not be established. $agi_calleridname
[$agi_callerid] --> $agi_dnid" >> /var/log/asterisk/trunk
# Reload trunk
/usr/sbin/asterisk -rx "sip reload"
# send email
echo -e "$MESSAGE" | mail -s "Incident at $HOST IP-PBX" "$EMAIL" -- -F "Asterisk"
Correct script ownership and permissions:
# chown asterisk:asterisk alarm.agi
# chown asterisk:asterisk iax2alarm.agi
# chmod +x alarm.agi
# chmod +x iax2alarm.agi
Check Permission:
ls -l
In /var/log/asterisk directory and create file trunk anc correct it’s ownership:
# > trunk
# chown asterisk:asterisk trunk
In FreePBX open trunks and select desired trunk.
Check Monitor Trunk Failures option and in the text box type alarm.agi:

Apply changes in FreePBX and you are ready.
Keep in mind that trunk will also be log rotated like other logs in /var/log/asterisk.
Author: Luis Rosario
Last update: 04-05-2020 02:19
Chan Spy
Source: http://www.freepbx.org/forum/chanspy-customization-in-freepbx
Edit File: extensions_override_freepbx.conf (For Permanent Effect)
extensions_additional.conf (For Tempotrary Effect)
Note: Authenticate(1234) - 1234 : is the password you want
[app-chanspy]
include => app-chanspy-custom
exten => 555,1,Authenticate(1234)
exten => 555,2,Read(SPYNUM,extension)
exten => 555,3,ChanSpy(SIP/${SPYNUM},q)
;old code
;exten => 555,1,Macro(user-callerid,)
;exten => 555,n,Answer
;exten => 555,n,Wait(1)
;exten => 555,n,ChanSpy()
;exten => 555,n,Hangup
; end of [app-chanspy]
Author: Luis Rosario
Last update: 04-05-2020 01:45
Monitoring Trunk Failures
SOURCE: http://zecic.com/monitoring-trunk-failures-in-freepbx/
Go into /var/lib/asterisk/agi-bin directory and create file alarm.agi and iax2alarm.agi.
Here is the content of the script:(NOTE: Modify SIP values for IAX values as required)
#!/bin/bash
EMAIL=luis@adnetgroup.com
DATE=date "+%d.%m.%Y. %H:%M"
HOST=hostname
# initializing agi variables
declare -a array
while read -e ARG && [ "$ARG" ] ; do
array=( echo $ARG | sed -e 's/://')
export ${array[0]}=${array[1]}
done
# SIP Trunk Status
SIPTRUNKS=/usr/sbin/asterisk -rx "sip show registry"
#Message
MESSAGE="Incident happend $DATE.\n$agi_calleridname [$agi_callerid]
tried to dial number $agi_dnid.\nCall could not be established on
channel $agi_channel."
MESSAGE="$MESSAGE\n\nCurrent SIP Trunk Status:\n$SIPTRUNKS"
# write log
echo "$DATE Call could not be established. $agi_calleridname
[$agi_callerid] --> $agi_dnid" >> /var/log/asterisk/trunk
# Reload trunk
/usr/sbin/asterisk -rx "sip reload"
# send email
echo -e "$MESSAGE" | mail -s "Incident at $HOST IP-PBX" "$EMAIL" -- -F "Asterisk"
Correct script ownership and permissions:
# chown asterisk:asterisk alarm.agi
# chown asterisk:asterisk iax2alarm.agi
# chmod +x alarm.agi
# chmod +x iax2alarm.agi
Check Permission:
ls -l
In /var/log/asterisk directory and create file trunk anc correct it’s ownership:
# > trunk
# chown asterisk:asterisk trunk
In FreePBX open trunks and select desired trunk.
Check Monitor Trunk Failures option and in the text box type alarm.agi:

Apply changes in FreePBX and you are ready.
Keep in mind that trunk will also be log rotated like other logs in /var/log/asterisk.
Author: Luis Rosario
Last update: 04-05-2020 02:19
SPEEDTEST
http://binarynature.blogspot.com/2013/03/measure-internet-connection-speed-from-linux-command-line.html
Install Application
yum -y install git
Step #1
mkdir -p ~/repo/remote; cd $_
Step #2
git clone https://github.com/sivel/speedtest-cli.git
Step #3
mkdir ~/bin
Step #4
cp ~/repo/remote/speedtest-cli/speedtest_cli.py ~/bin/speedtest-cli
Step #5
cp ~/repo/remote/speedtest-cli/speedtest_cli.py /usr/local/bin/speedtest-cli
Search for a Server
speedtest-cli --list | grep -i guaynabo
2135) CLARO-PRT (Guaynabo, Puerto Rico) [14.68 km]
3657) Open Mobile (Guaynabo, Puerto Rico) [14.68 km]
SeedTest
speedtest-cli --server 3657 --share
Author: Luis Rosario
Last update: 04-05-2020 02:01
Asterisk CLI via SSH or Web
Inside SSH Terminal Type
asterisk -rvv
BASIC "CLI" COMMANDS
TRUNKS REGISTRY
sip show registry
iax2 show registry
RELOAD TRUNKS
sip reload
iax2 reload
TRUNK & EXTENSIONS STATUS
sip show peers
iax2 show peers
Author: Luis Rosario
Last update: 04-05-2020 02:17
Music On Hold - Custom
PART I - WEB BASED INTERFACE
1) Login to PBX Server: voip.vonetoffice.com (Example)
Username: admin
Password: xxxxxx
2) Access TAB MENU: PBX
> Look On PBX Vertical Menu For: Internal Options & Configuration
> Under Internal Options & Configuration Menu Options Access: Music On Hold
3) Music On Hold: Delete/Remove all Files
4) Music On Hold: Upload New (.Wav) Files
IMPORTANT> Wave File Specs: 8000HZ / 16bit / Mono
5) If You Many Audio Files: Enable Random Play
PART II - SSH TERMINAL
1) Audio Files Path:
/var/lib/asterisk/mohmp3/
2) Default Audio Files to be Removed: All (.gsm) and (.wav)
IMPORTANT> Be Careful: Don't Delete New UPLOADED (.Wav) Files
Author: Luis Rosario
Last update: 04-05-2020 02:24
TDM400P - FXO/FXS Hardware Card (Zaptel / Dahdi)
1) Login to PBX Server: voip.vonetoffice.com (example)
Username: admin
Password: xxxxxx
2) Access TAB MENU: PBX
> Access SUB-MENU: Tools
> Select Tool: File Editor or/ Asterisk File Editor
Look, Found and Access: chan_dahdi.conf and dahdi-channels.conf
3) Modify Files:
chan_dahdi.conf
x; Auto-generated by /usr/sbin/hardware_detector
[trunkgroups]
[channels]
;context=from-pstn
context=from-zaptel <<< ***ADD CODE***
signalling=fxs_ks
rxwink=300 ; Atlas seems to use long (250ms) winks
usecallerid=yes
hidecallerid=no
callwaiting=yes
usecallingpres=yes
callwaitingcallerid=yes
threewaycalling=yes
transfer=yes
canpark=yes
cancallforward=yes
callreturn=yes
echocancel=yes
echocancelwhenbridged=no
faxdetect=incoming
echotraining=800
rxgain=0.0
txgain=0.0
callgroup=1
pickupgroup=1
;Uncomment these lines if you have problems with the disconection of your analog lines
busydetect=yes
busycount=3
immediate=no
#include dahdi-channels.conf
#include chan_dahdi_additional.conf
dahdi-channels.conf
; Autogenerated by /usr/sbin/dahdi_genconf on Fri Feb 18 16:50:46 2011
; If you edit this file and execute /usr/sbin/dahdi_genconf again,
; your manual changes will be LOST.
; Dahdi Channels Configurations (chan_dahdi.conf)
;
; This is not intended to be a complete chan_dahdi.conf. Rather, it is intended
; to be #include-d by /etc/chan_dahdi.conf that will include the global settings
;
; Span 1: WCTDM/4 "Wildcard TDM400P REV E/F Board 5" (MASTER)
;;;
signalling=fxs_ks
callerid=asreceived
group=0
;context=from-pstn
context=from-zaptel <<< ***ADD CODE***
channel => 1
callerid=
group=
context=default
;;;
signalling=fxs_ks
callerid=asreceived
group=0
;context=from-pstn
context=from-zaptel <<< ***ADD CODE***
channel => 2
callerid=
group=
context=default
Author: Luis Rosario
Last update: 04-05-2020 02:28
Linksys - PAP2 - Factory Reset
PAP2 Factory Reset
WARNING! If you're using an unlocked PAP2 previously supplied by Vonage, your adapter will revert back to the settings from the factory after resetting and will immediately attempt to 'phone home', re-provisioning itself from Vonage! If you'd like to reset your PAP2 then re-unlock it, make sure that you disconnect it from the Internet prior to performing a factory reset!
Resetting your PAP2 to its factory default settings (often referred to as a 'hard reset') is done via the built-in IVR (Interactive Voice Response) menu. To access the IVR, simply pick up a telephone that is connected to the PAP2 and dial:
* * * *
(yep, 4 stars) This will activate the IVR 'Configuration Menu' (you'll hear a voice tell you this) after which point, simply press the following sequence of keys to 'factory reset' your PAP2:
7 3 7 3 8 #
Funnily enough, the above key sequence spells 'R E S E T', followed by a #. You'll be asked to confirm your selection - simply press 1 to continue. That's it.
Author: Luis Rosario
Last update: 04-05-2020 02:31
DNS Cache - Asterisk
SOURCE: http://www.c2s.co.nz/blog/sc-installing-pdns-recursor-in-elastix/
Install DNS Recursor:
yum -y install pdns-recursor
Edit Config File:
nano -w /etc/pdns-recursor/recursor.conf
#################################
# allow-from If set, only allow these comma separated netmasks to recurse
#
# allow-from=127.0.0.0/8, 10.0.0.0/8, 192.168.0.0/16, 172.16.0.0/12, ::1/128, f$
allow-from=127.0.0.0/8
#################################
Restart Service:
/etc/init.d/pdns-recursor restart
Access PBX Web Interface:
Change > Network Parameters
Primary DNS: 127.0.0.1
Verify Changes:
cat /etc/resolv.conf
Author: Luis Rosario
Last update: 04-05-2020 02:46
Monitoring - Recording Files Access
How to create direct access to MONITORING folder to backup recorded files from PBX Server.
STEP #1 : ADD USER & PASSWORD
# adduser ******VONETPBX*****
# passwd *****PASSWORD*****
STEP #2 CREATE A SYMBOLIC FOLDER - MONITORING
# cd /home/vonetpbx
# ln -s /var/spool/asterisk/monitor monitor
# chown -h vonetpbx:vonetpbx monitor
STEP #3 TEST ACCOUNT - SFTP CONNECTION
You can use filezilla.org application client.
Author: Luis Rosario
Last update: 04-05-2020 02:51
STOP Recordings (Always Rec)
features_applicationmap_custom.conf
pauseMonitor => *881,peer/callee,StopMixMonitor()
globals_custom.conf
DYNAMIC_FEATURES=>pauseMonitor
SSH
asterisk -rx "dialplan reload"
asterisk -rx "features reload"
asterisk -rx "features show"
You must find the feature added in Dynamoc Feature list
Dynamic Feature Default Current
--------------- ------- -------
pauseMonitor no def *881
General Settings:
Asterisk Dial command options: trWW
Asterisk Outbound Dial command options: wW
Now on incoming call, press *8811 to stop the recording.
Author: Luis Rosario
Last update: 04-05-2020 02:57
Change default CentOS text editor from VI to Nano
SOURCE: http://www.khmer365.com/index.php?topic=3791.0
To change default VI Editor to Nano (Temporary)> Type the command as follows:
-
which nano
-
export EDITOR=/usr/bin/nano
-
crontab -e
To change default VI Editor to Nano (Permanent) > Type the command as follows:
nano /etc/profile
To change default VI Editor to Nano (Permanent) > ADD This Code to Profile:
export EDITOR=/usr/bin/nano
Author: Luis Rosario
Last update: 04-05-2020 03:19
Hotel - Management System
http://blogs.elastix.org/en/2010/03/how-to-hotel-management-system/
1) Installing the base system
First you’re going to need to ssh in to your Elastix PBX System.
Then, run the following:
cd /var/www/html
wget http://www.kefa.it/hotel.tar.gz
tar zxvf hotel.tar.gz
rm hotel.tar.gz
cd hotel
mysql -uroot -pPASSWORD < Hotel.sql
2) Updating the config
nano -w config.inc.php
Now you’re going to modify the following three paragraphs so that they match below:
//Hotel database
$dbhost = "localhost";
$dbpass = "PASSWORD";
$dbuser = "root";
$dbname = "Hotel";
//Asterisk database
$dbhost2 = "localhost";
$dbpass2 = "PASSWORD";
$dbuser2 = "root";
$dbname2 = "asterisk";
//Asteriskcdrdb database
$dbhost3 = "localhost";
$dbpass3 = "PASSWORD";
$dbuser3 = "root";
$dbname3 = "asteriskcdrdb"
Save and exit and you’re done with the config.
3) Fixing up HTTPS
nano /etc/httpd/conf.d/elastix.conf
MODIFY these line on elastix.conf file:
RewriteEngine Off
//////////// Second Option ///////////////////
# Redirect administration interface to https
RewriteEngine on
RewriteCond %{HTTPS} off
RewriteCond %{REQUEST_URI} !(/hotel/*) RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
Now, restart apache with:
/etc/init.d/httpd restart
You should now be able to access your WebGUI without HTTPS at:
http://pbxip/hotel/
If not, then go back and try again, as this part is crucial to the redirection to Reception when a phone is not Checked In
4) Updating dial-plan
Now we’re going to add in to the Dial-Plan and tell the PBX what calls can and cannot be made when the phone is not Checked-In.
nano /etc/asterisk/extensions_custom.conf
ADD the following underneath the [from-internal-custom] header:
;lets guests call other rooms without being checked in
;exten => _XXX,1,Dial(SIP/${EXTEN})
;exten => _XXX,n,Hangup()
;provide access to specific extensions without being checked in
exten => _128,1,Dial(SIP/${EXTEN})
exten => _128,n,Hangup()
exten => _13X,1,Dial(SIP/${EXTEN})
exten => _13X,n,Hangup()
exten => _14X,1,Dial(SIP/${EXTEN})
exten => _14X,n,Hangup()
exten => _15X,1,Dial(SIP/${EXTEN})
exten => _15X,n,Hangup()
exten => _5X,1,Dial(SIP/${EXTEN})
exten => _5X,n,Hangup()
;lets guests call freephonenumbers without being checked in
;exten => _1800NXXXXXX,1,Goto(outbound-allroutes,${EXTEN},1)
;exten => _1800NXXXXXX,n,Hangup()
exten => _X.,1,Set(result=${CURL(http://127.0.0.1/hotel/checkuser.php?Ext=${CALLERID(num)})})
exten => _X.,n,NoOp(Results: ${result})
exten => _X.,n,GotoIf($["${result}" = "OK"]?OK)
exten => _X.,n,GotoIf($["${result}" = "KO"]?KO)
exten => _X.,n(OK),Goto(outbound-allroutes,${EXTEN},1)
exten => _X.,n,Hangup()
;call front desk if not checked in
exten => _X.,n(KO),Dial(SIP/130) ; used for just one extension
;exten => _X.,n(KO),Goto(ext-group,2,1) ; used for ring groups
exten => _X.,n,Hangup()
;Hotel Management Configuration
exten => XXX,1,Dial(SIP/${DIAL})
exten => _X.,2,Macro(user-callerid,)
exten => _X.,3,Set(result=${CURL(http://127.0.0.1/hotel/checkuser.php?Ext=${CALLERID(num)})})
exten => _X.,4,NoOp(Results: ${result})
exten => _X.,5,GotoIf($["${result}" = "OK"]?OK)
exten => _X.,6,GotoIf($["${result}" = "KO"]?KO)
exten => _X.,7(OK),Goto(outbound-allroutes,${EXTEN},1)
exten => _X.,8,Hangup()
exten => _X.,9(KO),Dial(SIP/150) ; used for just one extension
;exten => _X.,n(KO),Goto(ext-group,2,1) ; used for ring groups
exten => _X.,10,Hangup()
Save the file and run:
asterisk -rx "dialplan reload"
Author: Luis Rosario
Last update: 04-05-2020 03:44
Call Recordings - Server Maintenance
1) Create Folder: mkdir /etc/recordingdeletion/
2) Create File Inside Folder: nano OldRecordingDeletion.sh
#!/bin/bash
# Change this path to reflect your recording storage
# location
RECORDINGS=/var/spool/asterisk/monitor
# Change this number to reflect the maximum age of call
# recordings
RECORDINGEXPIRY=14
# Change this number to reflect the maximum age of the
# deletion logs
LOGEXPIRY=25
# Current date
DATE=´date´
# Delete recordings older than $EXPIRY days
find $RECORDINGS -mtime +$RECORDINGEXPIRY > "removal-$DATE.log"
find $RECORDINGS -mtime +$RECORDINGEXPIRY -exec rm -f {} \;
# Delete log files older than $LOGEXPRY
find . -mtime +$LOGEXPIRY -name "*.log" -exec rm -f {} \;
3) Apply Permission: chmod +x OldRecordingDeletion.sh
4) Check Permission: ls -l
5) Create CRON JOB on Server: crontab -e
0 4 * * * /etc/recordingdeletion/OldRecordingDeletion.sh
6) Check CRON JOB Creation: nano /var/spool/cron/root
7) CRON JOB Log Files: tail -f /var/log/cron
Author: Luis Rosario
Last update: 04-05-2020 03:50
G729 / G723 Codecs - Installation (Open Source Version)
Source: http://www.blog.manhag.org/2010/05/installing-the-free-g729-codec-for-asterisk
Check Asterisk Version
Login to PBX Server: voip.vonetoffice.com (Example)
Username: admin
Password: xxxxxx
Access TAB MENU: PBX
> Access SUB-MENU: Tools
> Select Tool: Asterisk-Cli
Command: CORE SHOW VERSION
[Execute]
Common Used Codecs
Asterisk 1.4
codec_g723-ast14-gcc4-glibc-pentium4.so
codec_g729-ast14-gcc4-glibc-pentium4.so
codec_g723-ast14-gcc4-glibc-atom.so
codec_g729-ast14-gcc4-glibc-atom.so
Asterisk 1.6
codec_g723-ast16-gcc4-glibc-pentium4.so
codec_g729-ast16-gcc4-glibc-pentium4.so
codec_g723-ast16-gcc4-glibc-atom.so
codec_g729-ast16-gcc4-glibc-atom.so
1) Download Codec and Rename
Download: http://asterisk.hosting.lv
Rename:
codec_g723.so
codec_g729.so
2) Asterisk Server - Codec Upload Path:
/usr/lib/asterisk/module/
3) Restart Asterisk
/etc/init.d/asterisk restart
4) Login to PBX Server: voip.vonetoffice.com (Example)
Username: admin
Password: xxxxxx
5) Access TAB MENU: PBX
> Access SUB-MENU: Tools
> Select Tool: Asterisk-Cli
Command: core show translation
[Execute]
6) Asterisk Results
Translation times between formats (in microseconds) for one second of data
Source Format (Rows) Destination Format (Columns)
g723 gsm ulaw alaw g726aal2 adpcm slin lpc10 g729 speex ilbc g726 g722 siren7 siren14 slin16
g723 - 4999 1001 1001 3999 1001 1000 3999 11998 18998 - 4999 3000 - - 4999
gsm 13998 - 2001 2001 4999 2001 2000 4999 12998 19998 - 5999 4000 - - 5999
ulaw 11999 4000 - 1 3000 2 1 3000 10999 17999 - 4000 2001 - - 4000
alaw 11999 4000 1 - 3000 2 1 3000 10999 17999 - 4000 2001 - - 4000
g726aal2 12998 4999 1001 1001 - 1001 1000 3999 11998 18998 - 4999 3000 - - 4999
adpcm 11999 4000 2 2 3000 - 1 3000 10999 17999 - 4000 2001 - - 4000
slin 11998 3999 1 1 2999 1 - 2999 10998 17998 - 3999 2000 - - 3999
lpc10 13998 5999 2001 2001 4999 2001 2000 - 12998 19998 - 5999 4000 - - 5999
g729 14998 6999 3001 3001 5999 3001 3000 5999 - 20998 - 6999 5000 - - 6999
speex 14997 6998 3000 3000 5998 3000 2999 5998 13997 - - 6998 4999 - - 6998
ilbc - - - - - - - - - - - - - - - -
g726 13998 5999 2001 2001 4999 2001 2000 4999 12998 19998 - - 4000 - - 5999
g722 13998 5999 2001 2001 4999 2001 2000 4999 12998 19998 - 5999 - - - 1999
siren7 - - - - - - - - - - - - - - - -
siren14 - - - - - - - - - - - - - - - -
slin16 16998 8999 5001 5001 7999 5001 5000 7999 15998 22998 - 8999 3000 - - -
Author: Luis Rosario
Last update: 04-05-2020 03:56
Conference Calls - Recorded Files Storage
Recorded Conference Calls are SAVED on Server's Path:
/var/spool/asterisk/monitor
Author: Luis Rosario
Last update: 04-05-2020 03:58
Unblock IP from Fail2Ban
SOURCE: http://help.webcontrolcenter.com/KB/a1023/unblock-ip-from-fail2ban.aspx
http://richardjh.org/blog/unblocking-fail2ban-hosts/
https://www.howtoforge.com/how-to-whitelist-an-ip-in-fail2ban-on-debian-wheezy
Login as root user and run command:
#iptables -L -n
Fail2Ban Blocked IP's Results:
Chain fail2ban-SSH (1 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0
To removed blocked IP Address - Substitute on the command: Service Name + IP Address :
# iptables -D fail2ban-SSH -s 72.50.53.40 -j DROP
Fail2Ban IP WHITELISTING:
# nano /etc/fail2ban/jail.conf
Then, check the line > Add IP + Save Changes:
# ignoreip = 127.0.0.1 207.204.159.100/28 67.206.208.221/28
Restart Fail2Ban:
# service fail2ban restart
Author: Luis Rosario
Last update: 04-05-2020 04:08
Fail2ban - Install Summary
SOURCE: Seguridad en Servidores 0-8-6.pdf
Login as root user and run command:
yum install fail2ban
CHECKLIST file to be Modify & Create:
etc/fail2ban/jail.conf
etc/fail2ban/filter.d/asterisk.conf
etc/asterisk/logger.conf
etc/rc.d/init.d/fail2ban
Start/Re-Start Fail2Ban Service:
service fail2ban restart
Verify Fail2ban is running:
ps ax | grep fail2ban
Start Fail2ban Everytime Server Power-Up/Re-Start:
chkconfig fail2ban on
Verify Fail2Ban Config for Errors:
fail2ban-regex /var/log/asterisk/full /etc/fail2ban/filter.d/asterisk.conf
Author: Luis Rosario
Last update: 04-05-2020 04:13
Firewall-Iptables
SOURCE: Seguridad en Servidores 0-8-6.pdf
Login as root user and run command:
iptables -A INPUT -s 192.168.0.0/24 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 5060 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 4569 -j ACCEPT
iptables -A INPUT -i eth0 -p udp -m udp --dport 10000:20000 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 80 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 443 -j ACCEPT
iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 22 -j ACCEPT
iptables -A INPUT -p all -i eth0 -j DROP
Verify Rules:
iptables -L
Reset/Erase Rules if something gets wrong: "FLUSH"
iptables -F
SAVE Rules:
/sbin/service iptables save
IPTABLES CONFIG FILE:
nano /etc/sysconfig/iptables
EXTRA RULES - OPENFIRE
iptables -A INPUT -p udp -m udp -i eth0 --dport 9090 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 7777 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 5222 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 9090 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 7777 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 5222 -j ACCEPT
Author: Luis Rosario
Last update: 04-05-2020 04:17
Password Protect
nano /etc/httpd/conf.d/elastix.conf
<Directory "/var/www/html">
# Redirect administration interface to https
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
AuthType Basic
AuthName "PRIVATE ACCESS"
AuthUserFile /usr/local/apache/wwwpasswd
Require user elastix admin ciqala
</Directory>
mkdir /usr/local/apache
htpasswd –c /usr/local/apache/wwwpasswd admin
service httpd restart
EXTRA USERS
htpasswd /usr/local/apache/wwwpasswd ciqala
service httpd restart
Author: Luis Rosario
Last update: 04-05-2020 04:21
Removed VTiger CRM
Removed vtiger from the server
rpm -e elastix-vtigercrm
Author: Luis Rosario
Last update: 04-05-2020 04:23
Change SSH port 22 to another one
SOURCE: http://www.liquidweb.com/kb/changing-the-ssh-port/
Backup Current Setup:
cp /etc/ssh/sshd_config /etc/ssh/sshd_config_backup
Edit and Change SSH Port from 22 to 20022:
nano /etc/ssh/sshd_config
Firewall - Open New Port and Close Old Port:
Edit Firewall Rules + Reboot Firewall
Reboot SSH Service:
/etc/init.d/sshd restart
Author: Luis Rosario
Last update: 04-05-2020 04:26
LVM Partitions
SOURCE: http://www.how2centos.com/centos-lvm-resizing-guide/
STEP #1
lvresize -L +4GB /dev/VolGroup00/LogVol00
STEP #2
resize2fs -p /dev/VolGroup00/LogVol00
Author: Luis Rosario
Last update: 04-05-2020 04:29
HD Get Full By Log Files
Access and Verify Log Folder
cd /var/log/asterisk/
ls -lah
Removed / Delete Log Files (As You want)
rm LOGFILE NAME
Author: Luis Rosario
Last update: 04-05-2020 04:31
FOP2 - Different LAN CARD (eth0 is Default)
STEP #1 - Remover licencia / registro
If you plan to change network hardware or configuration, or reinstall your server, you *must* revoke the FOP2 license prior to that, with the command:
/usr/local/fop2/fop2_server --revoke
That action will free up your activation code to be used again after your changes/reinstallation.
STEP #2 - Registrar licencia via SSH
/usr/local/fop2/fop2_server --register -i eth1
STEP #3 - Configurar la tarjeta que utilizara FOP2
nano /etc/sysconfig/fop2
OPTIONS="-d -c /etc/asterisk/fop2 -i eth1"
service fop2 restart
Author: Luis Rosario
Last update: 04-05-2020 04:34
Adding Second HD (Hard Drive)
STEP #1 - Verify if Server detect HD
cat /proc/partitions
STEP #2 - Verify if HD is Mount
df -h
STEP #3 - Create HD Mount Point
mkdir /monitor
STEP #4 - Change Folder Permissions
chgrp asterisk /monitor
chown asterisk /monitor
ls -al
STEP #5 - Edit Server's Boot File
nano /etc/rc.local
ADD THIS CODE:
/bin/mount /dev/sdb1 /monitor
STEP #6 - Execute Server's Boot Script
cd /etc
./rc.local
STEP #7 - Verify HD Mounting Point
df -h
STEP #8- Verify Recording Location (To Backup Old Recordings)
cd /var/spool/asterisk/monitor/
ls
mv ./* /monitor
cd
STEP #9 - Removed Recording Folder + Create a Symbolic Link to New Folder
rm -rf /var/spool/asterisk/monitor
/bin/ln -s /monitor /var/spool/asterisk
STEP #10 - Verify Symbolic Link to New Folder
cd /var/spool/asterisk
ls -l
STEP #11 - Change Folder Permissions to Prevent Writing Errors
chown -h asterisk:asterisk monitor
ls -l
Author: Luis Rosario
Last update: 04-05-2020 04:47
How to list all DND-enable extensions
Source: http://www.mehrdust.com/archives/how-to-list-all-dnd-enable-extensions
in linux prompt run:
# asterisk -rx “database show DND”
# asterisk -rx “database show” | grep “/DND/”
# asterisk -rx "database show DND"
/DND/1002 : YES
/DND/1004 : YES
/DND/1006 : YES
/DND/1007 : YES
To remove DND from an extension run:
# asterisk -rx “database del DND ext.”
To enable DND manully for an extension run:
# asterisk -rx “database put DND ext. YES”
# asterisk -rx "database put DND 1002 YES"
Updated database successfully
# asterisk -rx "database show DND" /DND/1002 : YES
Author: Luis Rosario
Last update: 04-05-2020 04:56
LAN Card - Name Change
1) Removed & Rename the network interface configuration file :
cd etc/sysconfig/network-scripts/
rm ifcfg-eth0
mv ifcfg-eth1 ifcfg-eth0
2) Edit the network interface configuration file and replace all occurrences of the old name eth1 with the new one eth0 :
nano /etc/sysconfig/network-scripts/ifcfg-eth0
3) Removed & Rename the network interface configuration file :
cd etc/sysconfig/networking/devices
rm ifcfg-eth0
mv ifcfg-eth1 ifcfg-eth0
cd etc/sysconfig/networking/profiles/default
rm ifcfg-eth0
mv ifcfg-eth1 ifcfg-eth0
Author: Luis Rosario
Last update: 04-05-2020 05:12
Voicemail Recordings
Files Path
var/spool/asterisk/voicemail/default/100/
Author: Luis Rosario
Last update: 04-05-2020 05:15
Linksys/Cisco SPA3102
http://www.stephenwagner.com/?p=362
Author: Luis Rosario
Last update: 04-05-2020 05:17
How to setup network after RHEL/CentOS 7 minimal
https://lintut.com/how-to-setup-network-after-rhelcentos-7-minimal-installation/
Comandos básico de network en CENTOS 7
nmcli d
nmtui
service network restart
Author: Luis Rosario
Last update: 08-05-2020 01:55
Unblock IP from Fail2Ban
SOURCE: http://help.webcontrolcenter.com/KB/a1023/unblock-ip-from-fail2ban.aspx
http://richardjh.org/blog/unblocking-fail2ban-hosts/
https://www.howtoforge.com/how-to-whitelist-an-ip-in-fail2ban-on-debian-wheezy
Login as root user and run command:
#iptables -L -n
Fail2Ban Blocked IP's Results:
Chain fail2ban-SSH (1 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0
To removed blocked IP Address - Substitute on the command: Service Name + IP Address :
# iptables -D fail2ban-SSH -s 72.50.53.40 -j DROP
Fail2Ban IP WHITELISTING:
# nano /etc/fail2ban/jail.conf
Then, check the line > Add IP + Save Changes:
# ignoreip = 127.0.0.1 207.204.159.100/28 67.206.208.221/28
Restart Fail2Ban:
# service fail2ban restart
Author: Luis Rosario
Last update: 04-05-2020 04:08
Fail2ban - Install Summary
SOURCE: Seguridad en Servidores 0-8-6.pdf
Login as root user and run command:
yum install fail2ban
CHECKLIST file to be Modify & Create:
etc/fail2ban/jail.conf
etc/fail2ban/filter.d/asterisk.conf
etc/asterisk/logger.conf
etc/rc.d/init.d/fail2ban
Start/Re-Start Fail2Ban Service:
service fail2ban restart
Verify Fail2ban is running:
ps ax | grep fail2ban
Start Fail2ban Everytime Server Power-Up/Re-Start:
chkconfig fail2ban on
Verify Fail2Ban Config for Errors:
fail2ban-regex /var/log/asterisk/full /etc/fail2ban/filter.d/asterisk.conf
Author: Luis Rosario
Last update: 04-05-2020 04:13
Firewall-Iptables
SOURCE: Seguridad en Servidores 0-8-6.pdf
Login as root user and run command:
iptables -A INPUT -s 192.168.0.0/24 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 5060 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 4569 -j ACCEPT
iptables -A INPUT -i eth0 -p udp -m udp --dport 10000:20000 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 80 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 443 -j ACCEPT
iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 22 -j ACCEPT
iptables -A INPUT -p all -i eth0 -j DROP
Verify Rules:
iptables -L
Reset/Erase Rules if something gets wrong: "FLUSH"
iptables -F
SAVE Rules:
/sbin/service iptables save
IPTABLES CONFIG FILE:
nano /etc/sysconfig/iptables
EXTRA RULES - OPENFIRE
iptables -A INPUT -p udp -m udp -i eth0 --dport 9090 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 7777 -j ACCEPT
iptables -A INPUT -p udp -m udp -i eth0 --dport 5222 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 9090 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 7777 -j ACCEPT
iptables -A INPUT -p tcp -i eth0 --dport 5222 -j ACCEPT
Author: Luis Rosario
Last update: 04-05-2020 04:17
Password Protect
nano /etc/httpd/conf.d/elastix.conf
<Directory "/var/www/html">
# Redirect administration interface to https
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
AuthType Basic
AuthName "PRIVATE ACCESS"
AuthUserFile /usr/local/apache/wwwpasswd
Require user elastix admin ciqala
</Directory>
mkdir /usr/local/apache
htpasswd –c /usr/local/apache/wwwpasswd admin
service httpd restart
EXTRA USERS
htpasswd /usr/local/apache/wwwpasswd ciqala
service httpd restart
Author: Luis Rosario
Last update: 04-05-2020 04:21
Removed VTiger CRM
Removed vtiger from the server
rpm -e elastix-vtigercrm
Author: Luis Rosario
Last update: 04-05-2020 04:23
Change SSH port 22 to another one
SOURCE: http://www.liquidweb.com/kb/changing-the-ssh-port/
Backup Current Setup:
cp /etc/ssh/sshd_config /etc/ssh/sshd_config_backup
Edit and Change SSH Port from 22 to 20022:
nano /etc/ssh/sshd_config
Firewall - Open New Port and Close Old Port:
Edit Firewall Rules + Reboot Firewall
Reboot SSH Service:
/etc/init.d/sshd restart
Author: Luis Rosario
Last update: 04-05-2020 04:26
Magento Store Config File & Email Templates
Database Config
app/etc/local.xml
Email Templates
app/locale/en_US/template/email
Email Images
skin/frontend/default/default/images
Default Product Image
skin/frontend/default/theme/images/catalog/product/placeholder
Author: Luis Rosario
Last update: 04-05-2020 05:23
How to add a Contact Us form in Magento
Magento includes contact form functionality by default.
A link to a contact form can usually be found in the footer of your Magento installation.
Of course, you can add a contact form on any page. All you need to do is:
Paste the following code using the HTML option of the WYSIWYG editor:
<!– CONTACT FORM CODE BEGIN–>
{{block type='core/template' name='contactForm' template='contacts/form.phtml'}}
<!– CONTACT FORM CODE END–>
Save the changes and the contact form will appear on the desired page.
Author: Luis Rosario
Last update: 04-05-2020 05:26
How to disable the Compare products functionality
Edit app/code/core/Mage/Catalog/Helper/Product/Compare.php and change the following code:
public function getAddUrl($product)
{
return $this->_getUrl(’catalog/product_compare/add’, $this->_getUrlParams($product));
}
to
public function getAddUrl($product)
{
//return $this->_getUrl(’catalog/product_compare/add’, $this->_getUrlParams($product)); return false;
}
Edit ./app/design/frontend/base/default/layout/catalog.xml
(if you are using a different Magento theme, enter its name instead of default) and change the following code:
<block
name="catalog.compare.sidebar"
template="catalog/product/compare/sidebar.phtml"/>
to
<!-- <block
before="cart_sidebar" name="catalog.compare.sidebar"
template="catalog/product/compare/sidebar.phtml"/> -->
Flush the Magento cache from your Magento admin area > System > Cache Management.
Author: Luis Rosario
Last update: 04-05-2020 05:33





